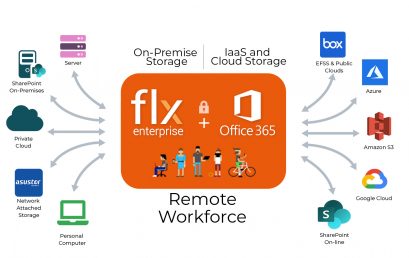
Key Benefits of Extending Office 365 with FileFlex Enterprise
Key Benefits of Extending Office 365 with FileFlex Enterprise Remote Access and Sharing Office 365 Files Today If you are using Office [...]
DETAIL
Extending Office 365 Functionality into a Hybrid-IT Infrastructure
How to add hybrid-IT zero-trust access, enhanced security, IT control and improved productivity to Office 365 What is Office? Microsoft Office [...]
DETAIL
How to Enable Your Remote Workforce with Zero Trust-By-Design
How to Enable Your Remote Workforce with Zero Trust-By-Design Instead of Traditional VPN The movement to enabling the remote workforce has […]
How to Mitigate Spear-Phishing via FileFlex Enterprise Zero Trust
How to Mitigate Spear-Phishing via the FileFlex Enterprise Zero Trust Platform FileFlex Enterprise is a remote access and sharing platform built [...]
DETAIL
FileFlex Enterprise is the Best Alternative to Varonis DatAnywhere
Varonis DatAnywhere will enter End of Life (EOL) in February 2020. That means that organizations that use DatAnywhere need to look for [...]
DETAIL
The CLOUD Act and the Importance of Keeping Data On-Premises
The U.S. government has announced its first bilateral agreement of the CLOUD Act with the U.K, This agreement will allow the U.K. […]
What is Centralized Cloud vs Decentralized Hybrid-IT?
The FileFlex decentralized hybrid-IT zero-trust computing architecture differentiates it from the centralized model used by all other file remote access and sharing platforms. [...]
DETAIL
How to Prevent Secret Data Exfiltration Inherent to Cloud Storage Solutions
What is the CLOUD Act? In order to combat the international nature of 21st century crime and make investigations by law enforcement […]
Addressing Cloud Computing Security Issues and Challenges – Part 3
Addressing cloud computing security issues and challenges is a complex subject and this series of blog posts barely scratches the surface. It […]
Addressing Cloud Security Issues – The Better Way – Part 2
Addressing cloud security issues can be daunting. In the first post of this series we saw that the cloud is simply a […]