
Addressing privacy and security issues in cloud computing is a complex topic, but one thing is for certain – copying your stuff to other people’s computers can be problematic. In the first post of this series we look at understanding what the cloud really is, how users lose control of their data, the concept of custodian and tenant, how cloud providers can access your data at any time and scanning / inspection for copyright infringement and illegal activity.
Ten years ago a cloud was a visible collection of water or ice particles suspended in the air. Today “the cloud” means more than something you see in the sky, now it is part of our everyday computing life. Although cloud computing and cloud storage are huge and it seems like every major computer company is involved, “the cloud” itself seems mysterious and industry descriptions don’t help. Take Apple for example and the iCloud. Here’s what the Apple.com website says about it.
“iCloud lets you access your music, photos, documents and more from whatever device you’re on. It’s easy to set up and use. And with features that give you peace of mind and make sharing simple, iCloud is also great with just one Apple device.”
Don’t you hate it when someone describes something by what it does instead of what it is? That is why for most of us, the cloud is something mysterious and confusing – and the reality is, because of jargon and use of nonsense, most people really don’t know what the cloud actually is.
What Is The Cloud Anyway?
A cloud is simply a computer where you store your files and documents over the internet. Before the cloud, you stored everything on your own computer. Before the cloud, you saved your files – your documents, spreadsheets, presentations, photos and videos – to your computer and your local hard drive. However, today we have tablets, smart phones and usually more than one computer. Storing a file on my local hard drive is useless when I want to work from my tablet or another computer. So what do we do, we simply save a copy of that file on the remote server of a cloud provider so that it can be accessed from any device that has an internet connection. We copy our stuff to someone else’s computer. When you understand it like this, you can understand that putting copies of your files on other people’s computers can be problematic.
Users Lose Control of Their Data
It doesn’t matter how good the technology of the cloud provider is or how big that provider is, issues of privacy and security of data are inherent in the use of the cloud itself. All the issues which we will discuss, start from the fact that the user loses possession of their data, because they store their data on a computer that belongs to someone else (the cloud provider). When you store your files on OneDrive, you are storing them on a computer owned by Microsoft. When you store stuff on Google Drive, you are copying them to a computer owned by Google. The same with Dropbox, Box and iCloud (Apple).
The Concept of a Tenant
Cloud providers use the concept of a custodian and tenant to describe the process of storing data on their servers. The custodian may look after the building, but the tenant owns the contents of their apartment. In the same way, according to cloud providers, you own the contents of what you store on their servers. The cloud however, is much more complex than a custodian and tenant and both the law and the practices of cloud providers make this a misleading metaphor because cloud providers reserve rights to the content you store on their servers, eroding your ownership, and the law doesn’t necessarily agree that your provider is just a custodian – they may consider the provider to be the owner of the data – completely eliminating your ownership of files stored in the cloud (see part 2 of this series).
Cloud Providers Can Access Data At Any Time
The service provider can access the data that is on the cloud at any time. There are many cases where they are required by law to do so, but they can do so at any time if they need to without the client’s authorization.
The Dropbox privacy policy states that:
We may disclose your information to third parties if we determine that such disclosure is reasonably necessary to (a) comply with the law; (b) protect any person from death or serious bodily injury; (c) prevent fraud or abuse of Dropbox or our users; or (d) protect Dropbox’s property rights.
Scanning and Inspection for Copyright Infringement and/or Other Illegal Activity
Did you know that cloud providers have systems in place to prevent you from using their service to share copyrighted content. This sounds quite reasonable until you realize that this means that they are scanning what you store and/or what you share and working with copyright holders to prevent piracy and other illegal activity. Here is a best-case example from Dropbox of what you can expect if you get caught.
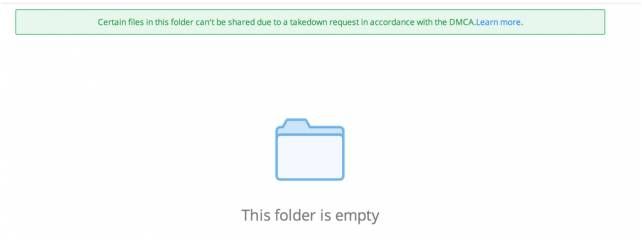
Worst case is that they inform the copyright holder or authorities of your behavior. Dropbox. Google and Amazon all say they will only dig into your files if someone tips them off to illegal or copyrighted material or to a law enforcement request. Microsoft on the other hand has come under fire for scanning user files and either restricting or closing accounts for content that was “questionable” even when in a private folder. Apple also reserves the right to scan your files stored in iCloud for illegal or malicious content.
Google states their policies in regards to copyright infringement as follows:
“We respond to notices of alleged copyright infringement and terminate accounts of repeat infringers according to the process set out in the U.S. Digital Millennium Copyright Act.
We provide information to help copyright holders manage their intellectual property online.”
Addressing Security Issues In Cloud Computing – The Better Way
When you copy your files to a cloud provider, you are in essence copying them to someone else’s computer. Copying your stuff to someone else’s computer can create problems, but there is a better way. The better way is this – stop it. Keep your files on your own storage, under your own control, behind your own firewall and on your own premises. Access, share or stream that content from its source location using FileFlex. You don’t need to copy anything to the cloud.
FileFlex Addresses Security Issues in Cloud Computing
FileFlex allows remote access, sharing and streaming of your own storage – all your storage – server storage, server attached storage such as NAS, SAN and DAS, desktops, laptops and FTP from any device, from anywhere.
It’s Free to Try
Why not try FileFlex yourself. We made it free to test drive. Check out the demo below or click here to see for yourself.
In Part 2 of this series we will look at the issues of legal jurisdiction, data residency, ownership and legal access by law enforcement.
Get it now
Get it now